How to Manage Password Policy Settings
As an Admin, the password policy settings allow you to enforce how users create, manage, and use passwords to ensure the maximum security of files in your organization.
To access your password policy settings:
1. Click on your profile icon and click on Administration Settings.
2. From the sidebar menu, click the Security tab.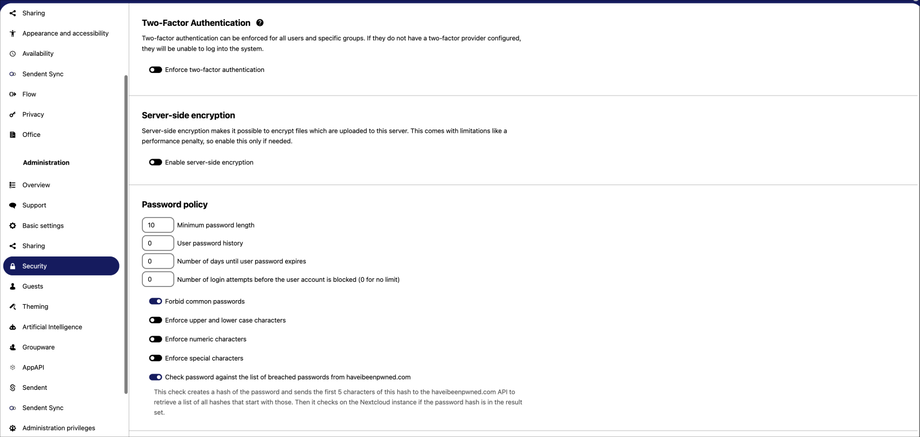
3. On the security page, navigate to the password policy section. In this section, you can do the actions below to enhance security: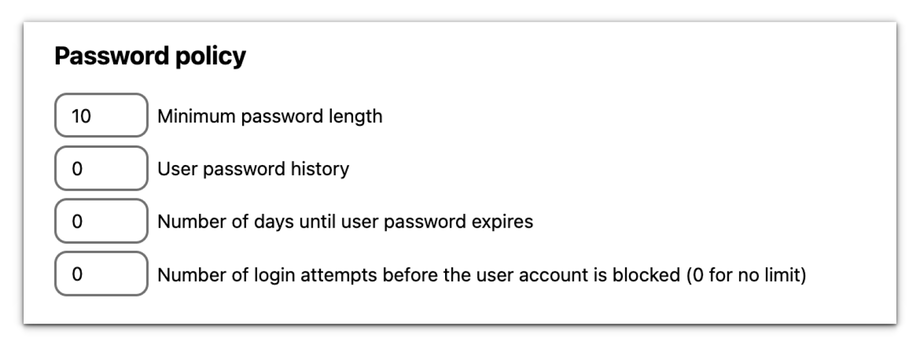
4. Set the minimum number of characters required for user passwords. This ensures that users create passwords of sufficient length, making them harder to guess or crack. For example, setting a minimum length of 10 characters can help enhance security.
5. Prevent users from reusing previous passwords by setting a history limit. Enter the number of previous passwords that cannot be reused. For instance, setting this to 5 means users cannot reuse any of their last five passwords, while 0 means there is no history enforcement.
7. Set the number of days until user passwords expire. Regularly expiring passwords and requiring users to create new ones helps mitigate the risk of long-term password exposure. For example, setting passwords to expire every 60 days can improve security.
8. Limit the number of failed login attempts before a user account is blocked. This helps prevent brute force attacks by locking accounts after a set number of incorrect attempts. For instance, blocking an account after 5 failed attempts can enhance protection.
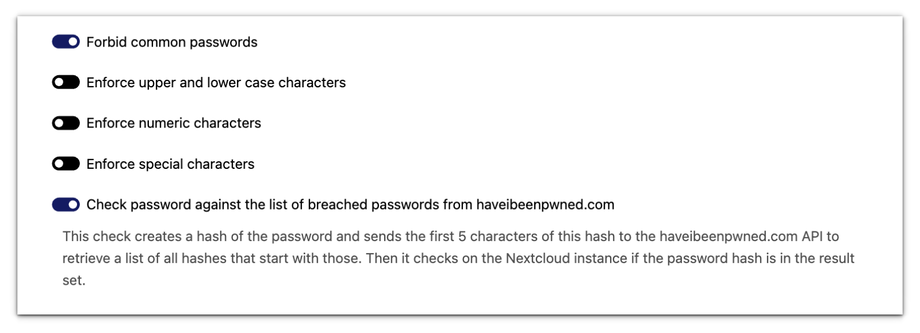
9. Forbid Common Passwords.
Prevent users from using common passwords. This reduces the risk of easily guessable passwords being used, which are often targeted by attackers. Examples of common passwords include "password123" or "123456."
10. Password Complexity.
-
Enforce Upper and Lowercase Characters: Require users to include both uppercase and lowercase letters in their passwords, increasing password complexity. For example, "SeCurEPassWorD" is stronger than "securepassword."
-
Enforce Numeric Characters: Require at least one numeric character in passwords, adding another layer of complexity. For instance, "Password1" is more secure than "Password."
-
Enforce Special Characters: Require at least one special character (e.g., !, @, #, $) in passwords, making them even harder for an attacker to guess. For example, "!P@ssword#1" is stronger than "Password1."
11. Breached Password Check.
Toggle the switch labeled Check password against the list of breached passwords from haveibeenpwned.com to enable this feature. When enabled, this check creates a hash of the password and sends the first 5 characters of this hash to the Haveibeenpwned.com API to retrieve a list of all hashes that start with those characters.
It then checks on the Nextcloud instance if the password hash is in the result set. If the password is found in the breached list, the user will be prompted to choose a different password.